Audit Risk Assessment: The Why and the How
By Charles Hall | Auditing
Today we look at one of most misunderstood parts of auditing: audit risk assessment.
Are auditors leaving money on the table by avoiding risk assessment? Can inadequate risk assessment lead to peer review findings? This article shows you how to make more money and create higher quality audit documentation. Below you’ll see how to use risk assessment procedures to identify risks of material misstatement. You’ll also learn about the risk of material misstatement formula and how you can use it to plan your engagements.
Audit Risk Assessment as a Friend
Audit risk assessment can be our best friend, particularly if we desire efficiency, effectiveness, and profit—and who doesn’t?
This step, when properly performed, tells us what to do—and what can be omitted. In other words, risk assessment creates efficiency.
So, why do some auditors (intentionally) avoid audit risk assessment? Here are two reasons:
- We don’t understand it
- We’re creatures of habit
Too often auditors continue doing the same as last year (commonly referred to as SALY)–no matter what. It’s more comfortable than using risk assessment.
But what if SALY is faulty or inefficient?
Maybe it’s better to assess risk annually and to plan our work accordingly (based on current conditions).
Are We Working Backwards?
The old maxim “Plan your work, work your plan” is true in audits. Audits—according to standards—should flow as follows:
- Determine the risks of material misstatements (plan our work)
- Develop a plan to address those risks (plan our work)
- Perform substantive procedures (work our plan) and tests controls for effectiveness (if planned)
- Issue an opinion (the result of planning and working)
Auditors sometimes go directly to step 3. and use the prior year audit programs to satisfy step 2. Later, before the opinion is issued, the documentation for step 1. is created “because we have to.”
In other words, we work backwards.
So, is there a better way?
A Better Way to Audit
During the initial planning phase of an audit, an auditor should do the following:
- Understand the entity and its environment
- Understand entity-level controls
- Understand the transaction level controls
- Use preliminary analytical procedures to identify risk
- Perform fraud risk analysis
- Assess risk
While we may not complete these steps in this order, we do need to perform our risk assessment first (1.-4.) and then assess risk.
Okay, so what procedures should we use?
Audit Risk Assessment Procedures
AU-C 315.06 states:
The risk assessment procedures should include the following:
- Inquiries of management, appropriate individuals within the internal audit function (if such function exists), others within the entity who, in the auditor’s professional judgment, may have information that is likely to assist in identifying risks of material misstatement due to fraud or error
- Analytical procedures
- Observation and inspection
I like to think of risk assessment procedures as detective tools used to sift through information and identify risk.
Just as a good detective uses fingerprints, lab results, and photographs to paint a picture, we are doing the same.
First, we need to understand the entity and its environment.
Understand the Entity and Its Environment
The audit standards require that we understand the entity and its environment.
I like to start by asking management this question: “If you had a magic wand that you could wave over the business and fix one problem, what would it be?”
The answer tells me a great deal about the entity’s risk.
I want to know what the owners and management think and feel. Every business leader worries about something. And understanding fear illuminates risk.
Think of risks as threats to objectives. Your client’s fears tell you what the objectives are–and the threats.
To understand the entity and its related threats, ask questions such as:
- How is the industry faring?
- Are there any new competitive pressures or opportunities?
- Have key vendor relationships changed?
- Can the company obtain necessary knowledge or products?
- Are there pricing pressures?
- How strong is the company’s cash flow?
- Has the company met its debt obligations?
- Is the company increasing in market share?
- Who are your key personnel and why are they important?
- What is the company’s strategy?
- Does the company have any related party transactions?
As with all risks, we respond based on severity. The higher the risk, the greater the response.
Audit standards require that we respond to risks at these levels:
- Financial statement level
- Transaction level
Responses to risk at the financial statement level are general, such as appointing more experienced staff for complex engagements.
Responses to risk at the transaction level are more specific such as a search for unrecorded liabilities.
But before we determine responses, we must first understand the entity’s controls.
Understand Transaction Level Controls
We must do more than just understand transaction flows (e.g., receipts are deposited in a particular bank account). We need to understand the related controls (e.g., Who enters the receipt in the general ledger? Who reviews receipting activity?).
So, as we perform walkthroughs or other risk assessment procedures, we gain an understanding of the transaction cycle, but—more importantly—we gain an understanding of controls. Without appropriate controls, the risk of material misstatement increases.
AU-C 315.14 requires that auditors evaluate the design of their client’s controls and to determine whether they have been implemented. However, AICPA Peer Review Program statistics indicate that many auditors do not meet this requirement. In fact, noncompliance in this area is nearly twice as high as any other requirement of AU-C 315 – Understanding the Entity and Its Environment and Assessing the Risk of Material Misstatement.
Some auditors excuse themselves from this audit requirement saying, “the entity has no controls.”
All entities have some level of controls. For example, signatures on checks are restricted to certain person. Additionally, someone usually reviews the financial statements. And we could go on.
The AICPA has developed a practice aid that you’ll find handy in identifying internal controls in small entities.
The use of walkthroughs is probably the best way to understand internal controls.
Sample Walkthrough Questions
As you perform your walkthroughs, ask questions such as:
- Who signs checks?
- Who has access to checks (or electronic payment ability)?
- Who approves payments?
- Who initiates purchases?
- Who can open and close bank accounts?
- Who posts payments?
- What software is used? Does it provide an adequate audit trail? Is the data protected? Are passwords used?
- Who receives and opens bank statements? Does anyone have online access? Are cleared checks reviewed for appropriateness?
- Who reconciles the bank statement? How quickly? Does a second person review the bank reconciliation?
- Who creates expense reports and who reviews them?
- Who bills clients? In what form (paper or electronic)?
- Who opens the mail?
- Who receipts monies?
- Are there electronic payments?
- Who receives cash onsite and where?
- Who has credit cards? What are the spending limits?
- Who makes deposits (and how)?
- Who keys the receipts into the software?
- What revenue reports are created and reviewed? Who reviews them?
- Who creates the monthly financial statements? Who receives them?
- Are there any outside parties that receive financial statements? Who are they?
Understanding the company’s controls illuminates risk. The company’s goal is to create financial statements without material misstatement. And a lack of controls threatens this objective.
So, as we perform walkthroughs, we ask the payables clerk (for example) certain questions. And—as we do—we are also making observations about the segregation of duties. Also, we are inspecting certain documents such as purchase orders.
This combination of inquiries, observations, and inspections allows us to understand where the risk of material misstatement is highest.
In a AICPA study regarding risk assessment deficiencies, 40% of the identified violations related to a failure to gain an understanding of internal controls.
Need help with risk assessment walkthroughs?
See my article Audit Walkthroughs: The What, Why, How, and When.
Get my new book:
Audit Risk Assessment Made Easy
Click here to see it on Amazon.
Another significant risk identification tool is the use of planning analytics.
Preliminary Analytical Procedures
Use planning analytics to shine the light on risks. How? I like to use:
- Multiple-year comparisons of key numbers (at least three years, if possible)
- Key ratios
In creating preliminary analytics, use management’s metrics. If certain numbers are important to the company, they should be to us (the auditors) as well—there’s a reason the board or the owners are reviewing particular numbers so closely. (When you read the minutes, ask for a sample monthly financial report; then you’ll know what is most important to management and those charged with governance.)
You may wonder if you can create planning analytics for first-year businesses. Yes, you can. Compare monthly or quarterly numbers. Or you might compute and compare ratios (e.g., gross profit margin) with industry benchmarks. (For more information about, see my preliminary analytics post.)
Sometimes, unexplained variations in the numbers are fraud signals.
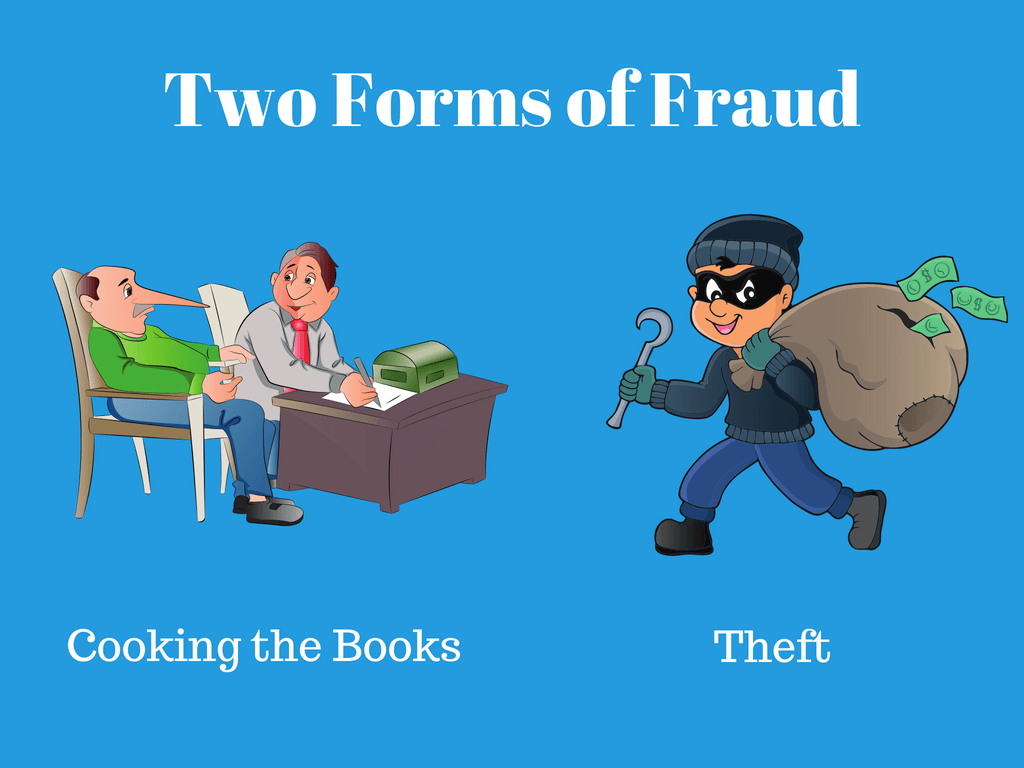
Identify Fraud Risks
In every audit, inquire about the existence of theft. In performing walkthroughs, look for control weaknesses that might allow fraud to occur. Ask if any theft has occurred. If yes, how?
Also, we should plan procedures related to:
- Management override of controls, and
- The intentional overstatement of revenues
My next post—in The Why and How of Auditing series—addresses fraud, so this is all I will say about theft, for now. Sometimes the greater risk is not fraud but errors.
Same Old Errors
Have you ever noticed that some clients make the same mistakes—every year? (Johnny–the controller–has worked there for the last twenty years, and he makes the same mistakes every year. Sound familiar?) In the risk assessment process, we are looking for the risk of material misstatement whether by intention (fraud) or by error (accident).
One way to identify potential misstatements due to error is to maintain a summary of the larger audit entries you’ve made over the last three years. If your client tends to make the same mistakes, you’ll know where to look.
Now it’s time to pull the above together.
Creating the Risk Picture
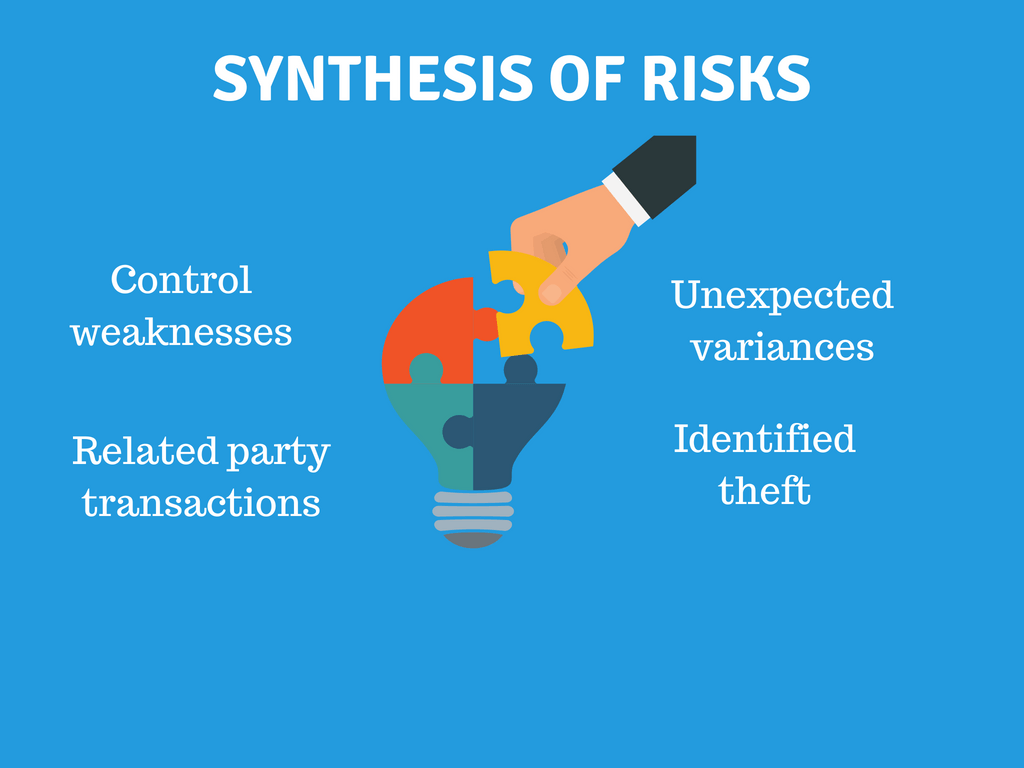
Once all of the risk assessment procedures are completed, we synthesize the disparate pieces of information into a composite image.
What are we bringing together? Here are examples:
- Control weaknesses
- Unexpected variances in significant numbers
- Entity risk characteristics (e.g., level of competition)
- Large related-party transactions
- Occurrences of theft
Armed with this risk picture, we can now create our audit strategy and audit plan (also called an audit program). Focus these plans on the higher risk areas.
How can we determine where risk is highest? Use the risk of material misstatement (RMM) formula.
Assess the Risk of Material Misstatement
Understanding the risk of material misstatement formula is key to identifying high-risk areas.
What is the risk of material misstatement formula?
Put simply, it is:
Risk of Material Misstatement = Inherent Risk X Control Risk
Using the RMM formula, we are assessing risk at the assertion level. While audit standards don’t require a separate assessment of inherent risk and control risk, consider doing so anyway. I think it provides a better representation of your risk of material misstatement.
Here’s a short video about assessing inherent risk.
And another video regarding control risk assessment.
Once you have completed the risk assessment process, control risk can be assessed at high–simply as an efficiency decision. See my article Assessing Audit Control Risk at High and Saving Time.
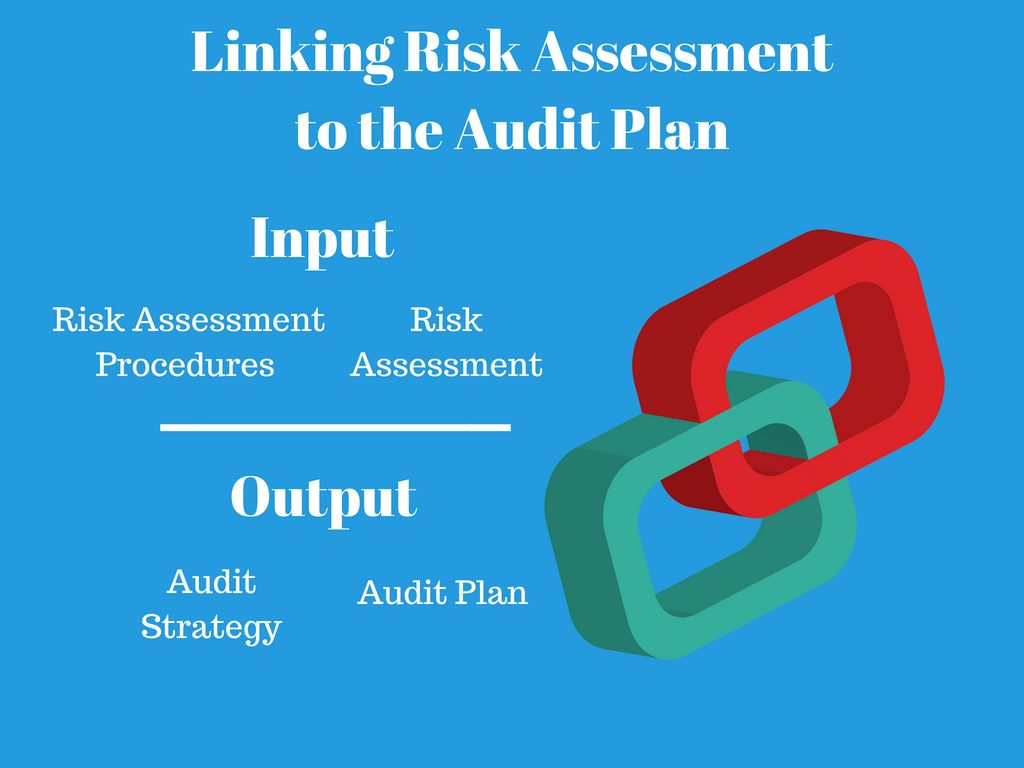
The Input and Output
The inputs in audit planning include all of the above audit risk assessment procedures.
The outputs (sometimes called linkage) of the audit risk assessment process are:
- Audit strategy
- Audit plan (audit programs)
We tailor the strategy and plan based on the risks..
In a nutshell, we identify risks and respond to them.
Next in the Audit Series
In my next post, we’ll take a look at Auditing for Fraud: The Why and How.
Audit Risk Assessment Made Easy – My New Book
My new book titled Audit Risk Assessment Made Easy is now available on Amazon. I’ve been working on this for over a year and a half. I think you’ll find it to be a valuable resource in understanding, documenting, planning, and performing risk assessment procedures.